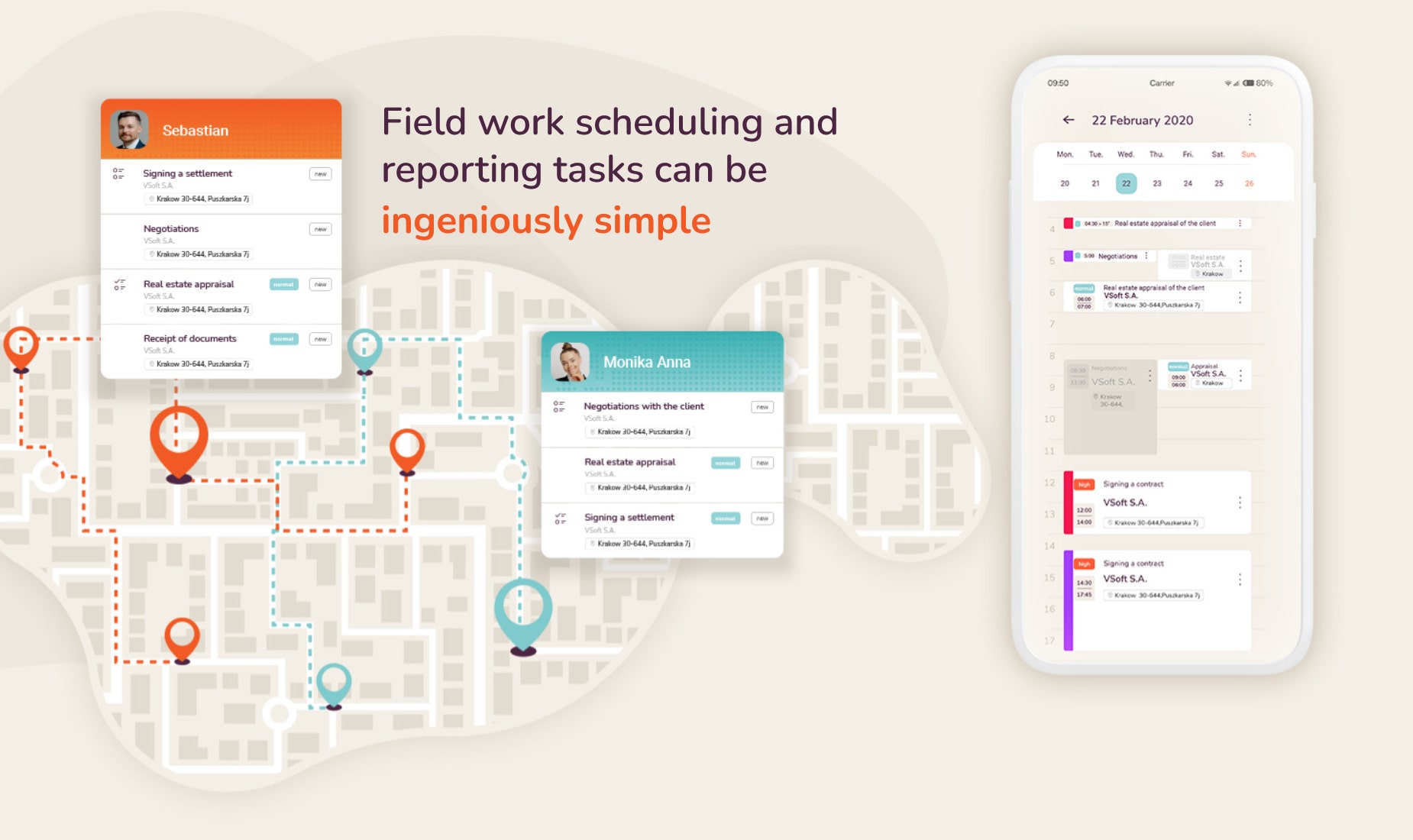
Main functionalities of the application
Complete task management done by field employeesSelected advantages of implementing the solution
![]() Up to 20% higher effectiveness of the field employees, due to possibility of planning and optimization of routes together with easy task reporting.
Up to 20% higher effectiveness of the field employees, due to possibility of planning and optimization of routes together with easy task reporting.
![]() Much shorter business process thanks to the on-line access to actual data during field tasks handling and instant reporting once the task is completed.
Much shorter business process thanks to the on-line access to actual data during field tasks handling and instant reporting once the task is completed.
![]() Employees security and control thanks to their location and route travelled monitoring.
Employees security and control thanks to their location and route travelled monitoring.
![]() Significant cost reductions thanks to employees accounting based on the visits done and routes travelled.
Significant cost reductions thanks to employees accounting based on the visits done and routes travelled.
![]() Personal data protection achieved through the encrypting and controlling of access; full auditability of access according to GDPR requirements.
Personal data protection achieved through the encrypting and controlling of access; full auditability of access according to GDPR requirements.
Security of the personal and financial data
Protection of the information available in the application is a key for us and we treat it as a complex work. We also provide full auditability of the access to data.
The OWASP/MASVS 1.0, level 2 requirements
The Mobile Workforce supports the security of data and user based on the global standards of the Open Web Application Security Project. Both administrator application and mobile application are secured according to the requirements of the ASVS 4 and mASVS 1 at the level 2.
Data encrypting
The communication between the application and server is encrypted thus no one will see what kind of data is send or downloaded. Effective distortion of your data makes it impossible to be used by third party. The SSL keys also authorize the connection between mobile application and server ensuring authenticity of the source.
Two factor secured access
Thanks to the additional verification in the process of new user registration, if one of the elements of login are being stolen, the third party will not get the access to your data.
Access and events logs in the system
All events taking place in the system (including log in) are registered and shown in a form of administrative logs. This allows for constant monitoring of users activity, as well as verification of possible undesirable attempts to access the application. From the desktop of administrator it is possible to verify how application works and diagnose a cause of errors.
Personal data deleting and anonymization
The application has the mechanism of the personal data anonymization according to the current law. Anytime, the administrator can call for the current scripts, which will permanently anonymize all personal data stored in a database.
How Kaczmarki Inkasso increased the effectiveness of field employees by 26%?
Case StudyThe effects that our clients enjoy are what drives us the most! Our cooperation with Kaczmarski Inkasso has been going on for many years now. With the Mobile Workforce application a team of over 50 mobile employees, performing a total of approx. 3,500 visits per month, increased efficiency by as much as 26%.
Watch the Case Study and learn more!












